Active Directory, JEA & Random Stuff – Acute @ HackTheBox
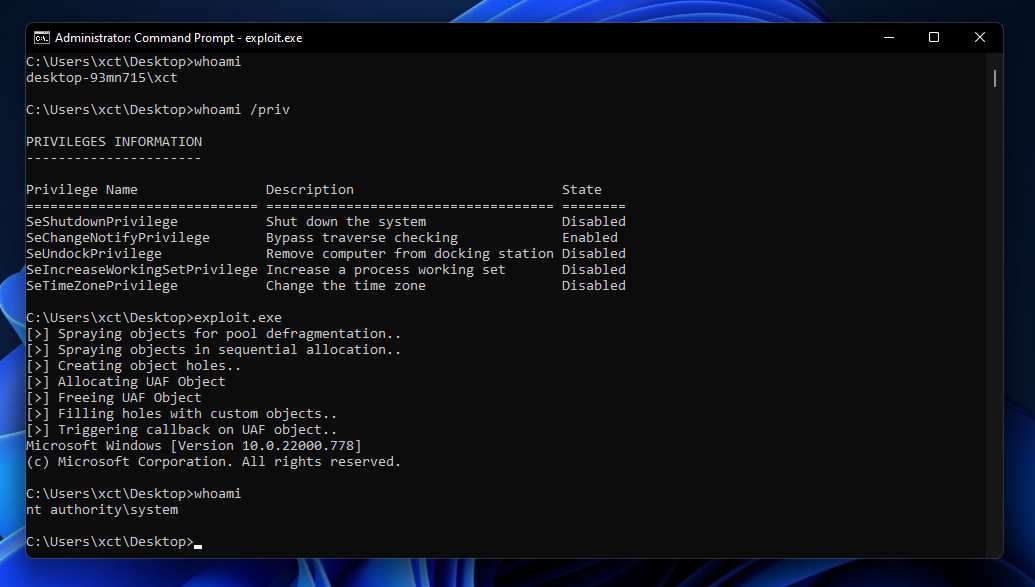
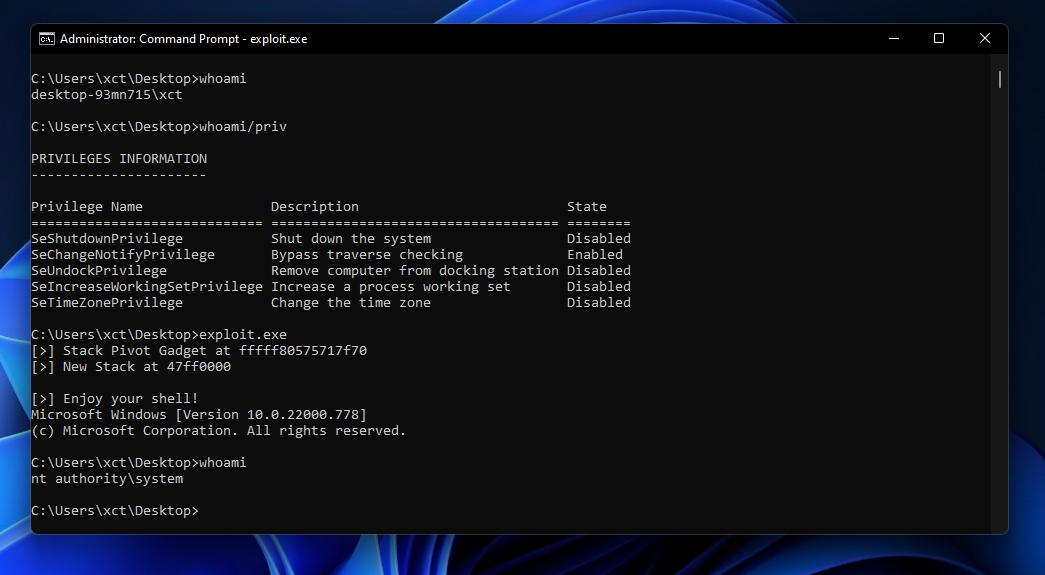
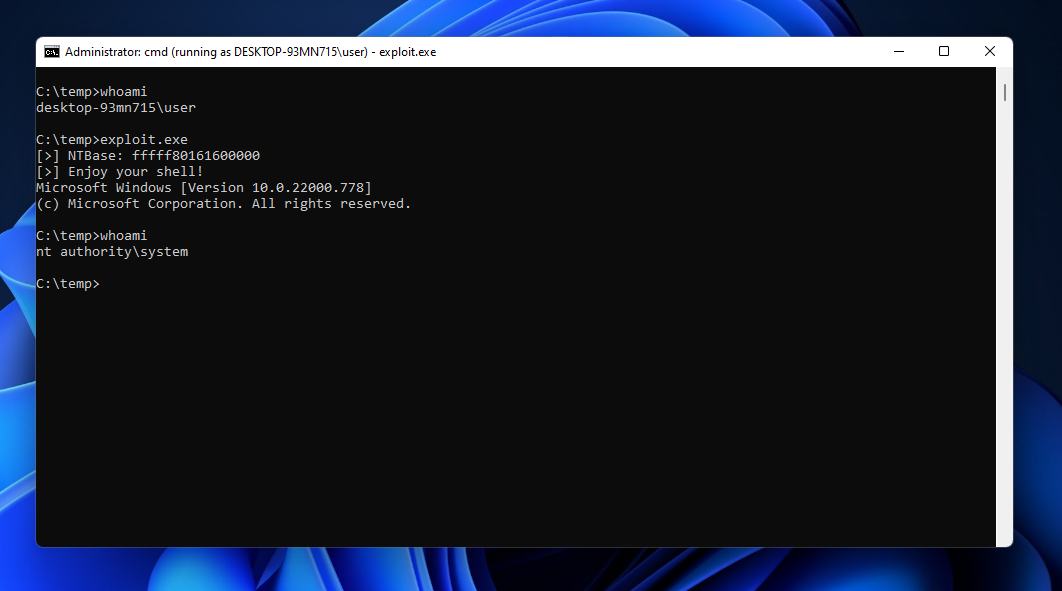
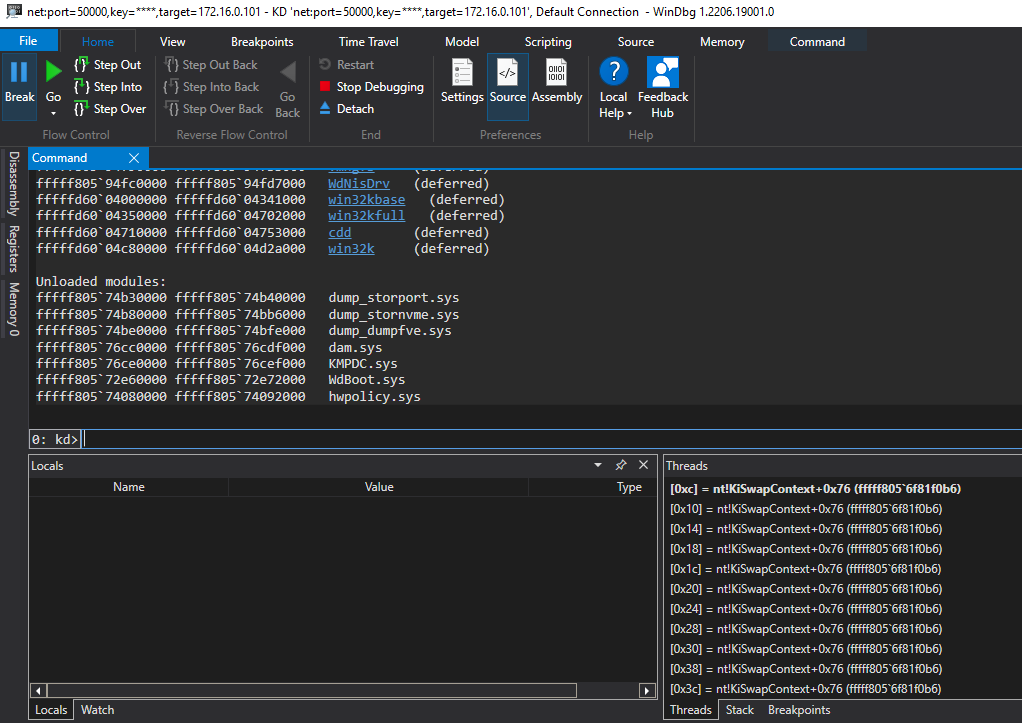
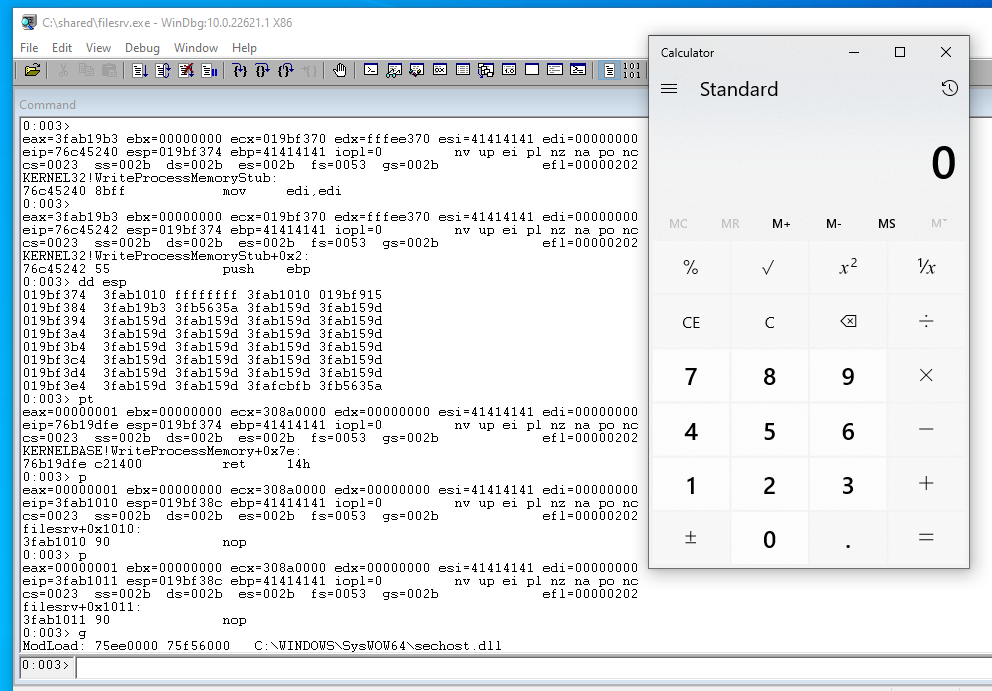
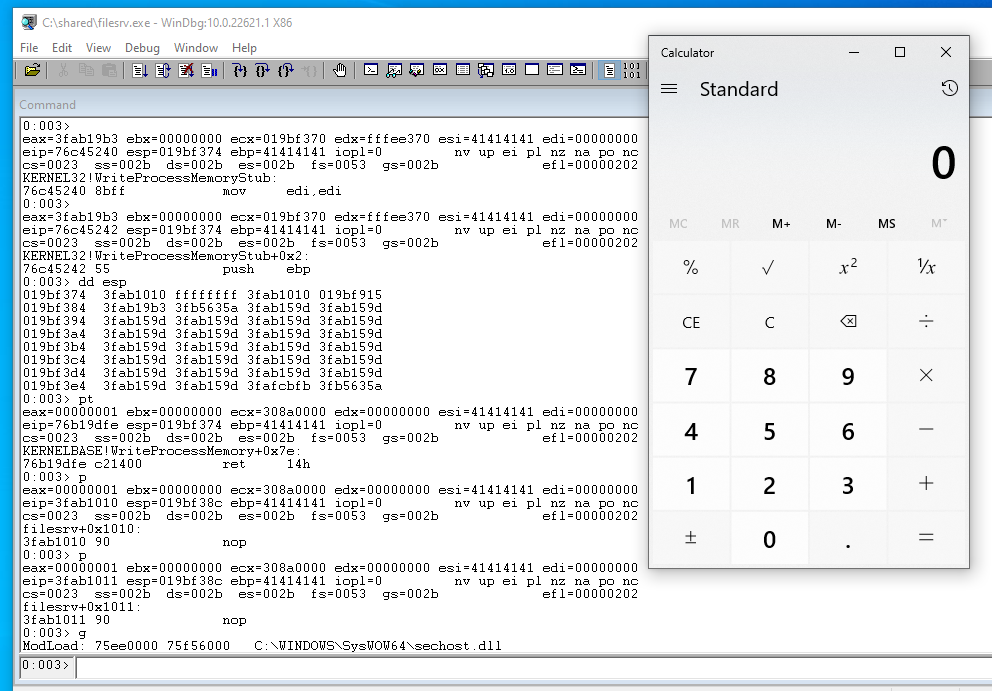
Acute is a 40-point Active Directory Windows machine on HackTheBox. I’m going to use it to show some techniques which can be useful in other scenarios and keep it short on the things that are not t...