
VL Shinra Part 4 - Reverse Engineering, Binary Exploitation & Ansible
This is part four of the Shinra series. We will get to access to a linux server via ssh, exploit a small authenticator app & use ansible to move to the next box.

This is part four of the Shinra series. We will get to access to a linux server via ssh, exploit a small authenticator app & use ansible to move to the next box.

This is the third video of the Shinra series. We will get a shell on Ashleighs machine & escalate privileges. Topics Phishing: Payload design & getting a shell Sliver Basics Host...

This is the second video of the Shinra series. Before setting foot onto any of the network’s internal machines, we are going to spend a bit of time enumerating various things from our machine. S...

This is a short writeup on the “NonHeavyFTP” challenge from Real World CTF 2023. This was one of the easier challenges with the goal of exploiting LightFTP in Version 2.2 (the latest one on github ...

This is the first video of a series about Shinra, a virtual company in a private red team lab. We will conduct a full pentest on Shinra and explore various topics along the way.

In this blog post, we will solve the Windows userland challenge that Blue Frost Security published for Ekoparty 2022. You can find the challenge & description here: https://twitter.com/blue...
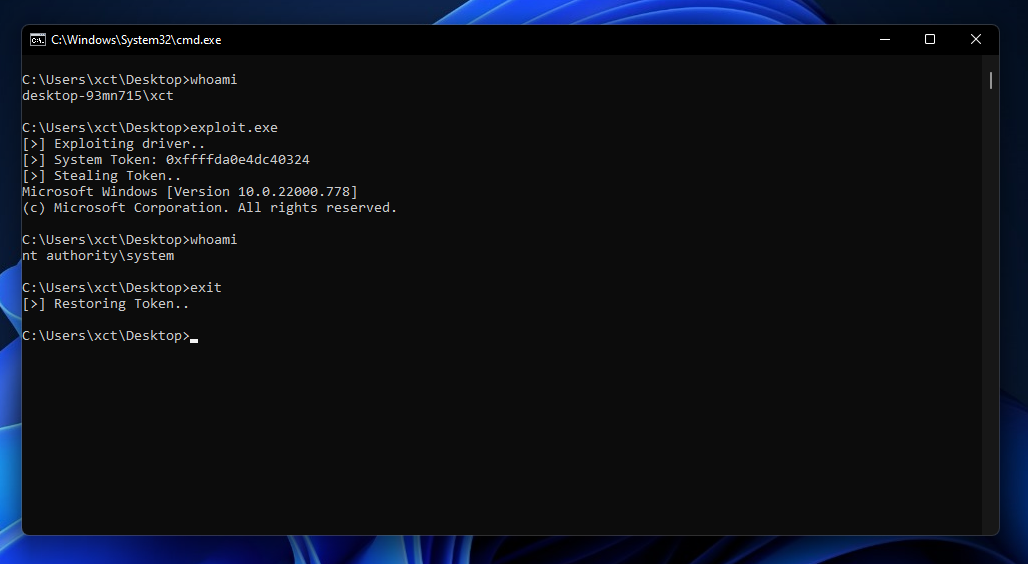
In this post, we will develop an exploit for the HW driver. I picked this one because I looked for some real-life target to practice on and saw a post by Avast that mentioned vulnerabilities in an ...
Additional notes for StreamIO, a medium difficulty Windows machine on HackTheBox that involves manual MSSQL Injection, going from file inclusion to RCE and in this case getting the SeImpersonate pr...

In this post, we will exploit Midenios, a good introductory browser exploitation challenge that was originally used for the HackTheBox Business-CTF. I had some experience exploiting IE/Edge/Chrome ...

Additional notes for Resourced, an intermediate difficulty Windows machine on PG-Practice that involves password spraying and an RBCD attack. Notes RBCD via WinRM & StandIn # Upload upload...